IT & Engineering
Password meters are not for humans
Mailgun takes the security of our users’ accounts very seriously, and when it comes to a compromise of an account - no one is having any fun. With so many things that can contribute to an account compromise, we took a step back to look at the various attack vectors used by bad actors trying to gain access to accounts.
PUBLISHED ON
We’re a couple of months into the new year, and as always, the fight against bad actors lives on.
Mailgun takes the security of our users’ accounts very seriously, and when it comes to a compromise of an account - no one is having any fun. With so many things that can contribute to an account compromise, we took a step back to look at the various attack vectors used by bad actors trying to gain access to accounts.
At the base of it all was one of the first things people set up when creating an account – their password. A strong password is critical for a good security posture, but coming up with a strong password can be a tedious task causing a lot of users to default to using simple and/or weak passwords. To protect them from compromise, we need to push them in the right direction.
Password Meters
When we initially sought out a new way to mitigate compromise via encouraging users to make better choices in creating passwords, we figured that having a password strength meter on the signup form was a good way to do this.
From here, we took a look at quite a number of existing examples to see what the industry is doing and since password strength meters are not new, what could be improved. Password meters typically consist of the following rules or requirements. Your password:
Must be at least eight characters or more
Must include at least one uppercase letter
Must include at least one lowercase letter
Must include at least one number
Must include at least one special character from a chosen set of acceptable symbols
The above rules are pretty standard, but they don’t work well.
Whenever someone talks about passwords, one commonly finds a reference to a particular comic talking about this very topic (this one here if you don’t know). There is a lot of material like this that does an excellent job at pointing out what we’re trying to get at here:
Humans are not good at making strong passwords.
While including all the rules above in your password may make it seem like you’re nudging people in the right direction, it doesn’t mean that it will be harder for computers to crack it. This is because people have very poor random generators installed in their heads. First of all, people typically use words that have special meaning to them. But, the human brain can also be primed to use associated words when exposed to a specific environment. The following Analysis of LinkedIn data breach is case in point:

Justifying Judgement
With that in mind, now we needed to answer how we would go about judging the strength of the password a user creates.
For starters, we found that the most effective way to mitigate account takeover due to insecure passwords is to check them against a database of hashed exposed credentials. The one we are utilizing ourselves comes from https://haveibeenpwned.com

If a user is trying to set an already exposed password, they shouldn’t be able to move forward in the flow. As an added benefit, this will hopefully encourage the user to change this password if they are using it for any other services.
So, we also mark passwords that are shorter than ten characters or include any information previously provided in the signup form domain name, actual name, company name, etc.
But, what if the password doesn’t exist in the exposed password hashes list and meets all other requirements but is something as simple as “Password0001!”?
Entropy
Another way to measure the strength of a password is to calculate its entropy. “Password entropy is a measurement of how unpredictable a password is. [It is] based on the character set[s] used...as well as password length” [1].
Usually measured in ‘bits,’ password entropy can be calculated by finding the entropy of each character, with a log base 2 of the number of characters in the character set used, multiplied by the number of characters within the password string itself.
When taking into account weak passwords that have yet to be leaked or cracked, using password entropy to render a message to a user via a password strength meter is useful to show them that they should consider using something better.
However, measuring the strength of a password-based just on its entropy is flawed.
For instance, let’s take the password “Password01!”, that is pretty common and could be easily guessed. What we see is that a naive password strength meter says otherwise:

This is a password strength meter that shows that this password is “Very Strong.” However, as is, this password has been seen on haveibeenpwned.com more than 400 times:

Here’s another example – let’s use a password consisting of five RANDOMLY SELECTED words, with each word varying in length of three to four passwords; no uppercase characters, no special symbols, and no numbers:

If you can’t make it out, the words are “fit”, “heat”, “scale”, “pot”, and “kneel.” In terms of entropy, this password has a smaller character set, but take a look at this:
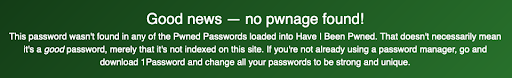
Although it’s measured out to be a “weak” password based on complexity, it hasn’t been pwned (as far as what we can see from haveibeenpwned.com’s response above.) When you take into consideration the number of permutations and combinations you have when choosing five words out of the number of three, four, and five letter words at random out of the English language for instance – it can be very complex. Let’s break it down:

Don’t take that too seriously though, as the nudge from HaveIBeenPwned suggests, just because it hasn’t been pwned doesn’t mean it’s a good password. This password is the kind of password you could lump together with that comic referenced earlier. Amongst the whole “correcthorsebatterystaple” type of passwords that suggest passwords like this are more memorable to humans while being harder for computers to crack due to the point above.
Overall: Unimpressive
So where am I going with this? We’re aware that the common requirements don’t work well, we know that password entropy in regards to coming up with a verdict of strength is a little flawed, so what do we do?
We make a password strength meter that is just unimpressed by anything you give it, that’s what.

Although our little, grouchy, unimpressed password strength meter feels like it’s still in a stage of infancy compared to what it could become later on, I feel that it’s the beginning of driving home a message.
One other thing that is an issue with most password strength meters is the overwhelming positive reinforcement they provide. While a password strength meter will yell at you that you haven’t met the requirements, as soon as you do meet those requirements you’re treated to positive responses to your choices and told almost explicitly that your password is the great and there’s nothing else needed to do that could help keep your account secure. In other words, you don’t need to worry, you will never be compromised.
Usual password strength meters work a lot like the first two bell curves you see in the image below:

Typically, once you meet requirements of a meter, you are thrown into the “It’s okay” or “Pretty good” areas and left at that which is not actually good or okay at all.

What we’re striving for is to be like the third bell curve you see above. Where we’re opposed to your choice of password most of the time and indifferent the rest. The reason being that just a password nowadays is not enough to be secure and as such the password meter shouldn’t be impressed.
Conclusion
All in all, making a good password strength meter is tricky and can lead users to making weaker passwords as opposed to better and stronger ones. As well, utilizing resources like haveibeenpwned.com to check for exposed passwords is much more robust compared to inventing and using your own strength-checking algorithms.
Utilizing a password manager that can generate passwords from a sufficiently large set of characters to achieve a desired level of entropy is one of the best options currently for creating strong and unique passwords. But, even so, you should still consider utilizing any and/or all other forms of security options available to you, such as security keys, authenticator apps, or any other available multi-factor authentication methods beyond using just a password.
Essentially, if you’re wondering whether you should implement a password strength meter on your site(s), I would say no unless you wanted to use it as some kind of vessel for a message. All a password meter is, really, is eye candy because we’ve made it almost impossible and inconvenient for humans to come up with a truly random password, if even possible.
And while we’ve engineered these meters to score the passwords we come up with, they are better used against ones that a computer can create because humans are just too predictable, even when we try our best not to be.
References:
[1] https://whatis.techtarget.com/definition/password-entropy
http://securitynirvana.blogspot.com/2012/06/linkedin-password-infographic.html





