Deliverability
5 phishing email warning signs
Phishing emails are becoming more and more sophisticated. It can be challenging to detect them, but there are warning signs to look out for that could protect you and your data. Here’s what you need to know.
PUBLISHED ON
If you suspect you have received a phishing email impersonating Mailgun, please send the email headers to abuse@mailgun.com.
When you get an email from a company that you recognize, you assume that the message you get is legitimate, why wouldn’t it be?. Unfortunately, scammers have gotten particularly good at tricking you. Now, you find that you have to second guess any password reset and updating billing emails you receive thanks to these phishing attempts. But as phishing evolves, so do our detective skills. Follow along in this blog as we walk through the top 5 phishing warning signs and learn how to spot these red flags for yourself.
Table of contents
Message headers
Landing page URL
Sense of urgency
Links and attachments
Strange wording
What are phishing emails?
Phishing attacks are emails designed to spoof legitimate businesses to gain your personal information. These emails lead to a deceptive landing page that asks you to input your personal data like your login or social security number, thus collecting your info.
A few years ago, these phishing attempts were easier to spot. Bad grammar, broken email templates, and outdated logos used to be the best hallmark signs for a phishing email. Spammers caught on that they needed to be craftier, and create more convincing phishing emails. Take a look at this email message:
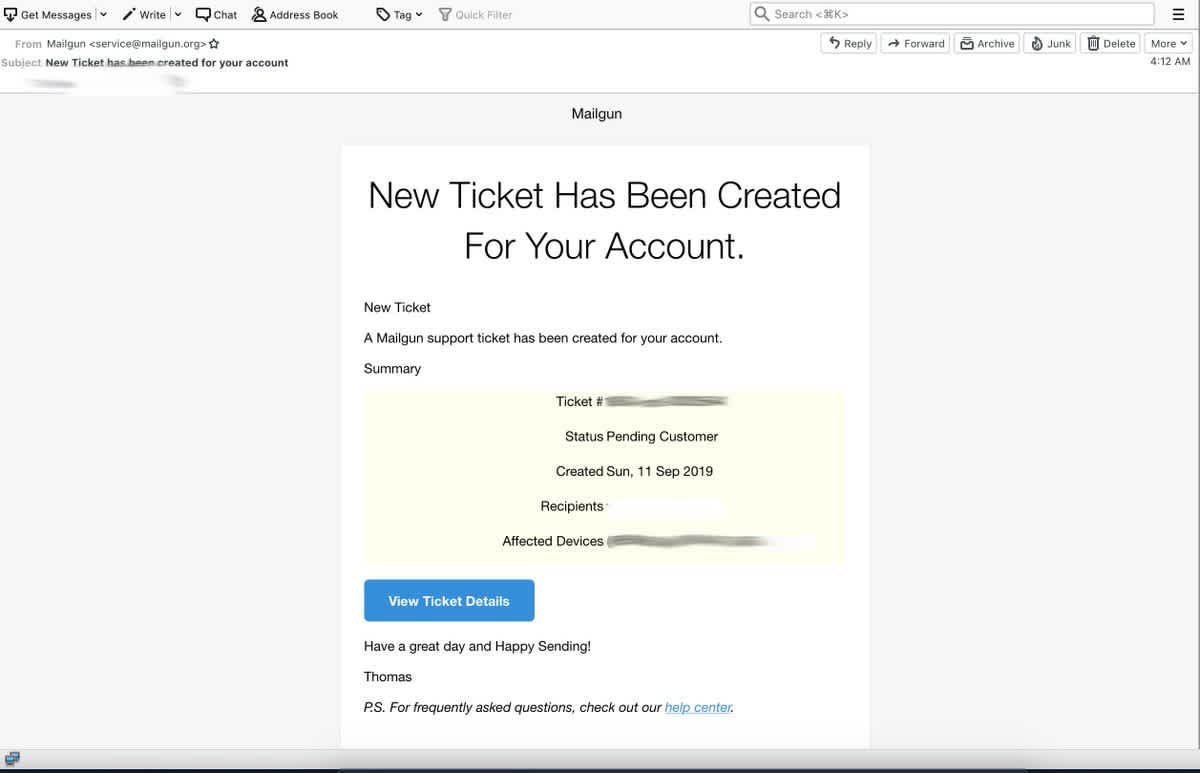
Pretty compelling, right? But wait, it gets worse. This is the landing page it sends you to if you click the link:
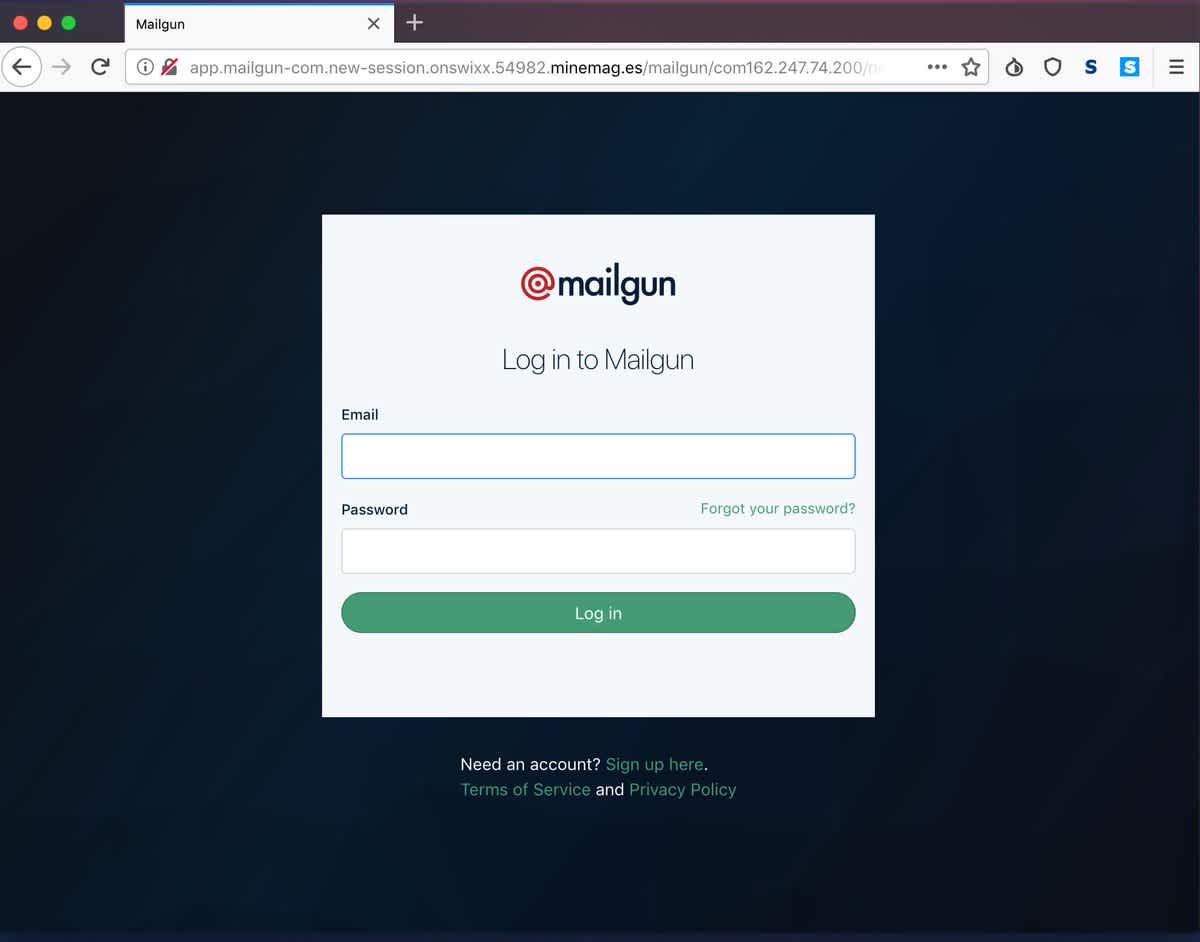
This can fool just about anyone into thinking that the email they received is legitimate. Even the smartest person can have an off day where they fall for an email like this, especially if the scammers are doing a decent job at impersonating a trusted company. Now the spammer has your login credentials, and you can get locked out of your account due to the compromise.
5 common signs of a sophisticated phishing attempt
Sometimes looking for spelling mistakes and formatting errors isn’t enough. If the spammer has really committed to their scam, they’ll do what it takes to make the email they send you look legitimate. Take for instance the email shown above, it looks like it came from Mailgun. The formatting on the email is a little off, but the biggest sign that jumps out to us is the from address. We as a company know that we don’t have a `service@mailgun.org` address, but not everyone is going to be privy to that information.
Message headers
Instead, we advise that you take a look at the message headers. These headers will give you every single last detail of a message – including who and where it’s actually coming from in the first place. You can usually find the headers by looking at the `more` options of a message, and clicking on `show original` from there, you will receive the headers.
For some, reading headers is second nature, but for those of you who aren’t looking at phishing and spam attempts all day, you can use tools like MXToolBox to parse the headers for you. If it doesn’t have the right authentications in place like DKIM tied to the message, it isn’t coming from the real sender.
Landing page URL
The URL of the landing page the email sends you to will always give away a phishing attempt. The example above is a bit tricky because the beginning of the URL looks pretty legitimate. It tries to trick you with the `mailgun-com,` hoping that your eyes will gloss over the fact that it isn’t our website. If that isn’t enough, the rest of the URL is just as bogus. Always be sure to double-check the URL anytime you are sent a message asking for personal contact information.
Sense of urgency
Part of the reason phishing attacks can be so successful are that they play on your need to resolve a problem by creating a false sense of urgency like “Your account will be closed in 24 hours”, “Your information is incorrect,” “We noticed unusual activity and your account is at risk”.
Phishing emails that create a sense of urgency will ask you for immediate action. This could be anything from following a link, inputting credit card details, or downloading a malicious file or attachment.
Links and attachments
In order to get your sensitive information and personal data, cyber criminals have to trick you into giving it up. We’ve shown you our landing page example, but another method is to convince you to download some kind of malware onto your computer. This allows scammers to gain access and steal your data another way. Look out for phrases like “download your bill” or “click this link to pay” that ask you to click a suspicious link.
Strange wording
Even though phishing scams are growing more and more sophisticated, poor grammar and strange wording are still signs of a spam email. Here are a few examples:
Dear costumer
We are able to offer you much better solutions
Important message form your bank
While spelling errors and sentence structure may be a dead giveaway, this is last on our list for a reason – AI can be used to write these scam emails. Since widespread, generative AI tools like ChatGPT are relatively new, we haven’t yet seen the full effects on the world of phishing. It’s important to remember that a scammer can’t spoof everything. So paying close attention to urls, domain names, sender addresses, and validating suspicious emails directly with the company they are impersonating are your first line of defense.
What else can you do?
Outside of being vigilant about phishing attempts, there are some added steps you can take to keep yourself and your data protected. For starters, make sure you have 2FA enabled on every account you have. This added security measure makes it much harder for spammers to access your information. Consider using password generators and password banks to update your passwords regularly, just in case you have to update your login credentials in a pinch.
Beyond that, it’s imperative that you inform the company that is being spoofed and the ESP the phishing email is coming from. Once they are made aware of the situation, the company in question and the ESP can work on mitigating the reach of spammers sending out those messages.
Want to learn what you can do as a sender to protect your recipients from phishing attacks? It’s all about building a strong sender reputation, and incorporating authentication best practices. Check out our guide on email authentication basics.
Should you suspect that you’ve received phishing attempts that look like they’re coming from Mailgun, please send your message headers to abuse@mailgun.com. We’ll take it from there.





